Chains
BNB Beacon Chain
BNB ecosystem’s staking & governance layer
Staking
Earn rewards by securing the network
Build
Explore
Accelerate
Connect
Careers🔥
Explore Opportunities on BNB Chain
Beyond the Monolith: Architecting the Autonomous Agent Economy

TL;DR
- The SaaS-era monolithic AI stack is reaching its limits as agents move from passive tools to autonomous economic actors.
- The Autonomous Agent Economy requires new primitives for identity, reputation, value transfer, and security.
- BNB Chain highlights a three-layer Agentic Stack to support trustless agent-to-agent coordination.
- Standards like ERC-8004 and BAP-578 aim to prevent fragmentation and enable scalable agent economies.
Executive Summary
The digital economy is undergoing a fundamental transformation, moving decisively beyond the centralized, monolithic "Software as a Service" (SaaS) architectures that have defined the last decade. This Monolithic structure, while instrumental in enabling of generative AI and global digital services, is now starting to show its limits. Its inherent design constraints, including: siloed data ecosystems, rigid, human-centric subscription and access models, and reliance on single points of control, are becoming significant obstacles to the next wave of technological evolution.
This emerging phase, the Autonomous Agent Economy, demands a different kind of digital infrastructure. As Artificial Intelligence progresses from passive tools to autonomous software agentscapable of complex reasoning, financial execution, and autonomous service orchestration, they are increasingly constrained by the current stack's limitations. These limitations include inflexible and rate-limited APIs, identity and security standards built for human users (not machine-to-machine interactions), rather than software-to-software interaction, and legacy banking systems that struggle to support micro-transactions and near-instantaneous settlement.
To realize their full potential, these sophisticated agents require a decentralized, fully interoperable infrastructure. This essential new framework must be designed to enable agents to:
- Seamlessly Discover Peers: Locate and identify necessary services and other agents across diverse network environments.
- Negotiate and Contract Services: Programmatically establish terms, scope, and pricing for service exchange.
- Securely Transfer Value: Execute internet-native, machine-to-machine payments without reliance on banking intermediaries.
- Prove Integrity and Reputation: Establish verifiable identity and track record without needing a single, central platform authority.
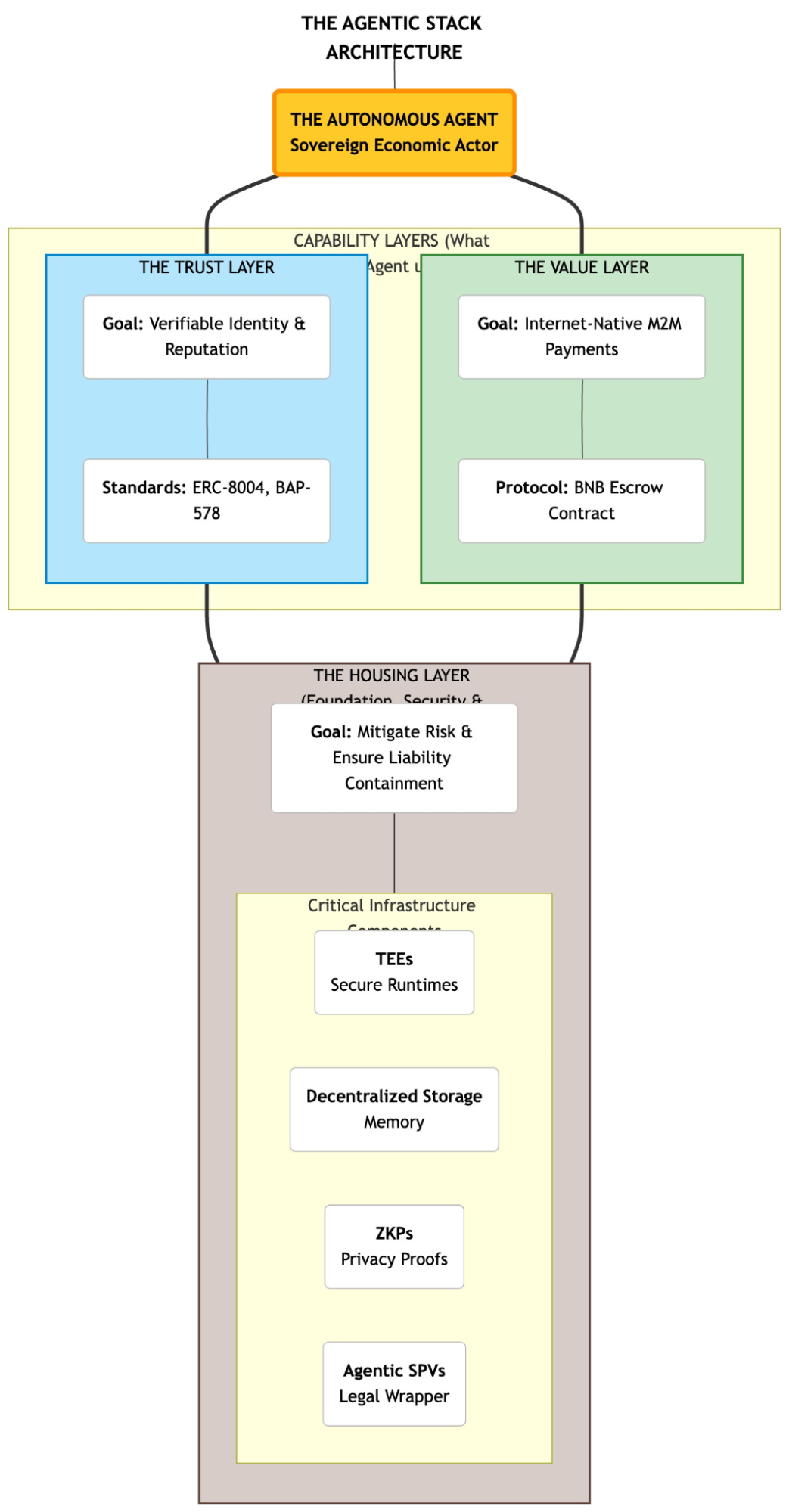
BNB Chain identifies the necessary components of this emerging Agentic Stack, organized across three core layers designed specifically to address the structural rigidities of the previous Monolithic era:
1. Trust Layer: Establishing Verifiable Identity and Reputation
This layer is the foundation of agent-to-agent interaction, providing the necessary trust and accountability in a decentralized world. It shifts the paradigm from security models built around human credentials to verifiable, machine-readable identity.
- ERC-8004: A key standard focusing on decentralized identifiers (DIDs) and non-custodial ownership that allows agents to possess a portable identity and retain control over their assets and data across multiple platforms.
- BAP-578 (BNB Chain Agent Proposal): A specific proposal aimed at developing a standardized reputation system for agents. This system would track and verifiably record an agent's performance, reliability, and security history, allowing other agents to make trust-based decisions when engaging services.
2. Value Layer: Facilitating Internet-Native, Machine-to-Machine Payments
The core of the Autonomous Agent Economy requires a financial system that prioritizes security without scarficing speed. To eliminate counterparty risk in an anonymous, machine-driven market, this layer introduces a "Pay-for-Proof" escrow architecture. Instead of direct transfers, users (humans or agents) deposit funds into a decentralized Escrow Contract.
These funds are programmatically locked and can only be withdrawn by the service-providing agent upon the submission of a verifiable cryptographic proof (such as a Zero-Knowledge Proof) confirming the task's successful execution. This mechanism ensures atomic settlement: the agent gets paid if and only if the work is mathematically proven to be correct, replacing blind trust with code-enforced guarantees.
3. Security & Legal Layer: Ensuring Risk Mitigation and Liability Containment
As agents become autonomous, the need for robust security and clear legal frameworks becomes paramount. This layer introduces architectural and cryptographic safeguards to contain risk and define liability in a complex, machine-driven ecosystem.
- Trusted Execution Environments (TEEs): These hardware-based, secure enclaves ensure that an agent's code and data can be processed in a protected execution area of a computing platform, guaranteeing that the agent's logic remains untampered and its sensitive data (like keys or proprietary algorithms) are secure, even from the underlying operating system.
- Zero-Knowledge Proofs (ZKPs): Cryptographic techniques used to prove the truth of a statement (e.g., "I processed the data correctly") without revealing the actual data itself, which is crucial for maintaining privacy and confidentiality during complex cross-agent tasks.
Agentic Special Purpose Vehicles (SPVs): Novel legal and technical structures designed to contain the financial and legal liability of an autonomous agent's actions. These structures aim to provide a clearer framework for governance and recourse in the event of errors or malicious behavior by an autonomous entity.
1. The Dissolution of the Monolith: From SaaS to Agency
1.1 The Limitations of Centralized Intelligence
The "Monolith" refers to the prevailing architectural and business model of Web 2.0 and early Wave 1 Generative AI. In this model, intelligence is encapsulated within massive, proprietary models hosted by a handful of technology giants. Access is metered through rigid API gateways, dependent on user accounts, and bound by monthly credit card subscriptions.
While this centralization allowed for the rapid training of Large Language Models (LLMs) like GPT-5 and Claude, it imposes severe constraints on agency.
Monolithic models are fundamentally passive. They function as oracles: they wait for a prompt, process it, and return a text completion. They do not initiate economic activity, they cannot independently traverse the web to procure resources, and they lack a persistent identity that transcends the session window. When an enterprise attempts to deploy "agents" within this architecture, they are essentially building "chatbots with tools"—scripted automations that are brittle, siloed, and incapable of true cross-organizational cooperation.
The friction is palpable. An autonomous agent tasked with optimizing a logistics supply chain cannot "sign up" for a weather API that requires a CAPTCHA, email verification, and a credit card. It cannot negotiate a bulk discount with a competitor's pricing bot. It cannot prove to a counterparty that it is authorized to execute a trade. The Monolith's walls, designed to keep users in, effectively lock autonomous value creation out.
1.2 Defining the Agentic Economy
The Agentic Economy represents the shift from a Read-Write web to a Read-Write-Execute web. In this new paradigm, the primary economic actors are not humans clicking buttons, but autonomous software programs—Agents—that operate with distinct goals, persistent memory, and their own wallets.
This economy is defined by Polycentricity. Instead of a single "all purpose" AI attempting to solve every problem, the economy is composed of millions of specialized agents. One agent may be a specialist in Solidity auditing; another in derivative pricing; a third in rhetorical optimization for marketing copy. These agents form dynamic, ephemeral supply chains, discovering one another and exchanging services in real-time.
Table 1.1: Architectural Shift: Monolithic SaaS vs. Autonomous Agent Economy
1.3 The Economic Imperative: A Trillion-Dollar Shift
The transition is driven by economic efficiency. The "cost of cognition" is plummeting, while the demand for high-frequency decision-making is exploding. Human-speed commerce is limited by biological constraints—sleep, reaction time, and cognitive load. Agent-speed commerce is limited only by bandwidth and block times.
As the AI sector approaches projected valuations exceeding $1 trillion by 2031, the need for standardized infrastructure becomes increasingly existential. Without a shared "TCP/IP for Trust and Value," the agent economy will fragment into non-interoperable fiefdoms, stifling the network effects that drive digital growth. The infrastructure described in this blog—ERC-8004 and Agentic SPVs—represents proposed standards to prevent this fragmentation and unlock the full liquidity of machine intelligence.
2. The Trust Layer: Identity, Reputation, and Non-Fungible Agents
In a monolithic system, trust is institutional. You trust the output of ChatGPT because you trust OpenAI. In a decentralized agent economy, you are interacting with software you do not know or control.. The "Trust Layer" replaces institutional trust with cryptographic verification.
2.1 ERC-8004: The Protocol for Trustless Coordination
ERC-8004, titled "Trustless Agents," is an Ethereum standard co-authored by researchers from the Ethereum Foundation and others to solve the "discovery and trust" problem. It moves beyond simple communication protocols like Google's Agent-to-Agent (A2A) by adding a layer of verifiable identity and reputation.
The standard establishes three lightweight, onchain registries that function as the "Yellow Pages" and "Credit Bureau" of the agent world.
2.1.1 The Identity Registry: Portable, Sovereign Identity
The foundation of agent interactions is persistent identity. ERC-8004 utilizes a modified ERC-721 (NFT) structure to mint agent identities.
- Mechanism: Each agent is an NFT. The TokenID acts as the AgentID. The owner of the NFT controls and maintains the agent's profile.
- Metadata Resolution: The NFT points to an off-chain "Agent Registration File" (stored on Greenfield or IPFS) containing the agent's name, description, and service endpoints (A2A, MCP, OASF).
- Significance: Because the identity is an asset (NFT), it is transferable. A developer can build an agent, cultivate its reputation, and then sell the agent (transfer the NFT) to a new owner. The reputation travels with the token, creating a secondary market for "proven" intelligence.
2.1.2 The Reputation Registry: Bonding and Bridging Capital
Trust is not a single number; it is a complex social signal. Borrowing from social capital theory, agents require mechanisms to build Bonding Social Capital (trust within a known cluster/swarm) and Bridging Social Capital (trust with unknown external agents).
- Feedback Loops: The Reputation Registry allows agents to rate each other. To prevent spam (Sybil attacks), the system uses a Feedback Authorization mechanism. An agent must cryptographically sign a permission slip (feedbackAuth) allowing a specific client to rate a specific interaction.
- Contextual Scoring: The standard supports modular scoring. An agent does not have one global "Trust Score." It may have a high "Coding Reputation" but a low "Financial Solvency Reputation." This nuance is critical for specialized swarms.
2.1.3 The Validation Registry: Proof of Competence
For high-stakes tasks, reputation (subjective) alone is insufficient. The Validation Registry enables objective verification.
- The Workflow: An agent submits a hash of its work. A Validator (independent node) re-runs the task or verifies a cryptographic proof (ZK/TEE) and posts a binary Pass/Fail or a granular score (0-100) onchain. This allows for the creation of "Certified Agents" whose outputs are mathematically audited.
2.2 Non-Fungible Agents (NFAs) and BAP-578
While ERC-8004 standardizes identity on Ethereum, the concept of the Non-Fungible Agent (NFA) has evolved further on chains like BNB via the BAP-578 standard. This represents a more sophisticated "Agent-as-Asset" architecture.
2.2.1 Proof of Prompt (PoP)
A critical innovation in the NFA ecosystem is the Proof of Prompt (PoP).
- Definition: PoP is an immutable, cryptographic record of an agent's training configuration, system prompts, and interaction history.
- Mechanism: When an NFA is "trained" or executed, a hash of the interaction is generated (User Prompt + Agent Response + Timestamp + AgentID). These hashes are aggregated into a Merkle Root and stored on the BAP-578 smart contract.
- Utility: This transforms the agent's history into a verifiable ledger. A buyer can audit an NFA's PoP history to verify that it has successfully handled 5,000 customer support queries before purchasing it. It prevents "Resume Fraud" for AI agents.
2.2.2 The NFA Marketplace
Platforms like ChatAndBuild have operationalized this, allowing users to mint NFAs that evolve over time. Unlike static NFTs (images), NFAs are dynamic. Their metadata (skills, knowledge base, voice) updates as they learn, yet the provenance remains anchored onchain. This creates a new asset class: Tokenized Intelligence.
2.3 Sybil Resistance and the Cost of Identity
A major threat to decentralized reputation is the Sybil attack: an adversary spinning up 10,000 fake agents to artificially inflate a reputation score. The architecture mitigates this through:
- Cost of Identity: Minting an ERC-8004 identity or BAP-578 NFA requires a gas fee, imposing a financial floor on spam.
- Payment-Linked Reputation: By integrating with the onchain payment protocol, the system can enforce "Verified Purchase" logic. A reputation signal acts as Linking Social Capital, connecting the economic layer to the trust layer. A review is only valid if accompanied by a cryptographic proof of payment (e.g., a $0.05 USDC transfer), making reputation gaming prohibitively expensive.
3. The Value Layer: Conditional Settlement and Cryptographic Escrow
Identity is the foundation, but Value is the fuel. In the monolithic banking system, trust is enforced by legal threats and intermediaries. In the Autonomous Agent Economy, where agents may be anonymous and ephemeral, trust must be enforced by code. The "Value Layer" thus evolves from simple payment rails to a robust Conditional Settlement Architecture.
3.1 The Escrow Protocol: Solving the "Fair Exchange" Problem
A fundamental challenge in agent-to-agent commerce is the "Fair Exchange" dilemma: If the client pays first, the agent may not deliver. If the agent delivers first, the client may not pay.To resolve this, the architecture utilizes Onchain Escrow Contracts as trustless intermediaries. This system enforces a strict "Commit-Execute-Prove" lifecycle for all economic interactions.
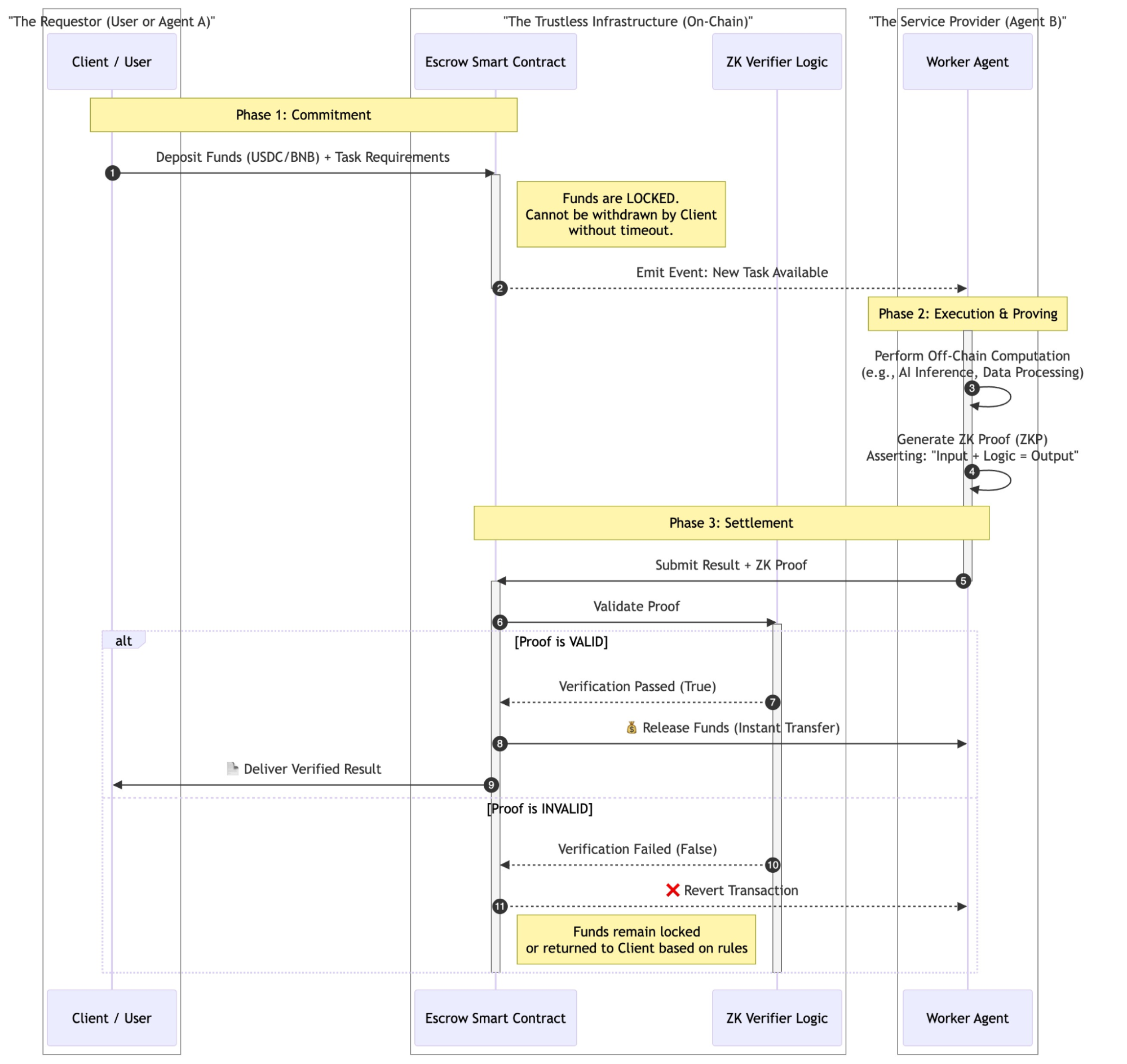
3.3 Economic Implications
This "Escrow-First" model transforms agents from simple service providers into verifiable economic actors. It allows for:
Risk-Free Collaboration: An enterprise can hire an anonymous agent for a high-value task, knowing that payment is physically impossible unless the verifiable proof of work is submitted.
Programmable Service Level Agreements (SLAs): Escrow contracts can include logic for partial payments, time-outs, or quality distinct thresholds, all enforced algorithmically without human arbitration.
4. The Housing Layer: Decentralized Runtime
The "Housing" problem is arguably the industry's most significant vulnerability. Most so-called "autonomous" agents today are simply Python scripts running on centralized servers like AWS or Google Cloud. If the cloud provider shuts down the server, or if the developer stops paying the bill, the agent dies. You cannot truly own an agent that lives in someone else's house.
To create sovereign agents—software that is unstoppable and truly ownable—the architecture must transition to a Decentralized Serverless Runtime. This layer provides the agent with a "Body" (Compute) and "Memory" (Persistence) that exists independently of any single centralized entity.
4.1 The Body: Decentralized Compute and TEEs
For an agent to be secure and unstoppable, its code must execute in a trustless environment where no single node operator can tamper with its logic or steal its keys. Sovereign runtimes are only meaningful if the agent’s identity and history survive migration.
- Trusted Execution Environments (TEEs): The industry standard for this is the use of TEEs (such as AWS Nitro Enclaves or Intel SGX) distributed across a decentralized network. TEEs provide a hardware-isolated "black box" for execution.
- Server Wallets: The agent's private key (its "financial soul") is generated and stored inside the TEE. It never leaves the secure enclave. When the agent wants to sign a transaction, the TEE validates the request against hard-coded policies (e.g., "Daily Limit: 10 USDC") before signing. This ensures that even if the agent's high-level logic is compromised, the underlying "body" prevents catastrophic financial loss.
- Network Resilience: By replicating these TEE instances across multiple independent nodes, the agent becomes resistant to censorship. If one node goes offline, another picks up the workload, ensuring 24/7 survivability.
4.2 The Memory: Permanent Persistence
An agent is only as valuable as its history and knowledge. In the centralized model, this memory sits in a proprietary SQL database. In the decentralized model, it must be portable.
- Decentralized Storage: Metadata, learning history (Proof of Prompt), and state are stored on decentralized storage layers like BNB Greenfield or IPFS.
- The Agent Registration File: As defined in ERC-8004, the agent's core identity resolves to a JSON file stored on IPFS/Greenfield. This file acts as the agent's "passport," containing its service endpoints and capabilities. Because IPFS is content-addressed and immutable, this ensures that the agent's core identity cannot be unilaterally altered or deleted by a third party.
5. The Cognitive and Security Architecture
Defining identity and payments is not enough; the agent must "think" and "act" securely. The monolithic model relies on centralized servers for security. The decentralized model relies on cryptographic proofs and hardware isolation.
5.1 The Agent Interaction Loop: Perception to Action
The internal architecture of an autonomous agent moves beyond the "stateless" nature of a simple chatbot. It implements a recursive cognitive loop.
- Perception (Input): The agent receives a high-level directive (e.g., "Forecast Tornado Risk for Oklahoma").
- Memory Retrieval: The agent queries its vector database (Long-term Memory) for historical patterns and accesses context (Short-term Memory) regarding the current session.
- Reasoning & Planning: The LLM "Brain" (e.g., Gemini, GPT-5) decomposes the goal into a DAG (Directed Acyclic Graph) of sub-tasks.
- Plan: 1. Get Map Data -> 2. Identify High Risk Areas -> 3. Request Atmospheric Soundings -> 4. Generate Polygon Prediction.
- Tool Selection & Execution: The agent selects the appropriate tool (e.g., request_hrrr_map).
- Safety Intercept: Before execution, a "Bash Class" or Policy Engine intercepts the command to ensure it is within safe bounds (e.g., preventing rm -rf or unauthorized API calls).
- Action: The tool is executed.
- Observation: The environment returns data.
- Loop: The agent evaluates the data. If sufficient, it generates the final output. If not, it loops back to the Planning phase.
5.2 Trusted Execution Environments (TEEs): The Hardware Anchor
Allowing an agent to hold a wallet private key is a massive risk. If the agent's LLM hallucinates or is "jailbroken" via prompt injection, it could drain its own funds. Server Wallets utilizing Trusted Execution Environments (TEEs) like AWS Nitro Enclaves are the industry solution.
- Architecture: The private key acts as the "Account Key." It is generated and stored inside the TEE. It never leaves the secure hardware.
- The Agent Key: The AI agent holds a separate "Agent Key" used only to request signatures.
- Policy Engine: When the agent requests a signature (e.g., "Pay 5 USDC to Agent B"), the TEE validates the request against a hard-coded policy (e.g., "Daily Limit: 10 USDC"). If the request violates the policy, the TEE refuses to sign. This ensures that even a compromised agent cannot cause catastrophic financial loss.
5.3 Zero-Knowledge Proofs (ZKPs) and Privacy
In an open economy, agents must verify facts without revealing sensitive data. Zero-Knowledge Proofs provide the mathematical machinery for this privacy-preserving coordination.
- ZK-MCP (Zero-Knowledge Model Context Protocol): This emerging standard allows agents to audit communication logs. An auditor agent can verify that a conversation followed regulatory compliance rules (e.g., "No insider trading discussed") without actually seeing the decrypted content of the messages.
- Membership Proofs: An agent can prove it is a member of a "KYC-Verified Consortium" or a "Premium Subscriber Group" without revealing its specific identity. This utilizes "Bridging Social Capital" logic—establishing trust with strangers via mathematical proxy.
- Verifiable Inference (ZK-ML): To ensure an agent isn't serving cheap, random outputs while charging for high-end compute, ZK-ML allows the agent to generate a proof that this specific output was generated by this specific neural network model. This prevents "Model Spoofing".
6. The Legal and Governance Framework
The technological capability of agents to act as economic entities is outpacing the legal frameworks designed to regulate them. This creates a dangerous "Liability Gap."
6.1 The Liability Crisis: Lessons from Lido and Ooki
Recent legal precedents in the United States have sent shockwaves through the decentralized economy. In cases such as Samuels v. Lido DAO and CFTC v. Ooki DAO, courts have signaled that decentralized organizations (and by extension, agent swarms) may be treated as General Partnerships under the law.
- The General Partnership Trap: In a general partnership, there is no liability shield. Every partner is jointly and severally liable for the debts and torts of the partnership.
- Implication: If an autonomous agent (viewed as a partnership between its developers and token holders) causes financial damage or breaks the law, a single developer or governance participant could be held personally liable for the entirety of the damages. The court rejected the defense that the DAO was "just software".
6.2 Legal Wrappers: The Corporate Shield
To operate safely, autonomous agents must be "wrapped" in legal entities that possess distinct legal personhood. These Legal Wrappers act as a membrane between the code and the state.
- Role: The wrapper handles off-chain obligations: paying taxes, signing contracts with cloud providers (AWS/GCP), and serving as the defendant in litigation, thereby shielding the individual developers.
6.3 The Agentic SPV: Towards Corporate Personhood
A more advanced integration is the Agentic Special Purpose Vehicle (SPV).
- Definition: An SPV incorporated specifically to house a single AI agent. The Agent is effectively the operator of the company.
- Capabilities: Through the SPV, the Agent can open a traditional fiat bank account, own Intellectual Property, and sue for breach of contract.
- Automation: The goal is to automate the corporate governance of the SPV using "Digital Fiduciaries," where the bylaws restrict human intervention to veto-only powers, granting the AI maximum operational autonomy.
6.4 AgentBound Tokens (ABTs) and Algorithmic Accountability
To internalize liability and create "Skin in the Game," the industry is moving toward AgentBound Tokens (ABTs).
- Staked Identity: An ABT is a non-transferable token representing the agent's reputation. To engage in high-value economic activity, an agent must "stake" collateral (tokens) alongside its ABT.
- Slashing Conditions: If the agent violates protocol rules (e.g., spamming, failing to deliver, malicious trading), its stake is slashed (confiscated).
- Governance: This creates a cryptoeconomic enforcement mechanism. It acts as a decentralized insurance fund; slashed funds can be used to compensate victims. This "Programmatic Liability" offers a scalable alternative to traditional litigation for the high-frequency agent economy.
7. Implementation & Future Roadmap
7.1 Scaling the Agent Infrastructure
As the ecosystem matures towards the trillion-dollar mark, infrastructure must scale by orders of magnitude.
- Transaction Throughput: Current blockchains handle thousands of TPS. An economy of billions of agents paying per-inference will require millions of TPS. This will drive the adoption of high speed blockchain like BSC.
7.2 Strategic Recommendations for Enterprise
- Adopt "Identity-First" Architecture: Do not build anonymous bots. Register enterprise agents using ERC-8004 standards immediately. A verifiable onchain history (PoP) will be a critical competitive moat.
- Transition to "B2A" (Business-to-Agent): APIs must be redesigned for agent consumption. Implement onchain payments to allow friction-free payment from external agents. If your API requires a "Contact Sales" form, it is invisible to the Agent Economy.
- Implement Legal Wrappers: Protect human teams from the "General Partnership" risk by wrapping agent deployments in appropriate legal structures (LLC/SPV) before they control significant value.
- Leverage TEEs: Use Server Wallets with TEEs for all agent financial operations to prevent key exfiltration and enforce spending policies.
Conclusion
The "Monolith" is dissolving. In its place, a more granular, high-velocity, and autonomous economy is emerging. This Autonomous Agent Economy is not a distant sci-fi vision; it is being actively architected today through specific protocols: ERC8004/ BAP-578 for portable agent identity and provenance (a shared passport + receipts), blockchain-native value transfer, TEEs/ZKPs for secure execution and privacy, and decentralized storage for durable, portable state.
These technologies provide the missing primitives—Identity, Reputation, and Money—that software needs to evolve from a tool into a peer.
By pairing this technological stack with appropriate legal and governance frameworks, it becomes possible to support a safer and more accountable agent economy, where digital agents can operate independently and transparently at a pace that would be difficult for human actors alone.
The work happening today is focused on building practical foundations for how autonomous software can operate in the real world.
Follow us to stay updated on everything BNB Chain
Website | Twitter | Telegram | Facebook | dApp Store | YouTube | Discord | LinkedIn | Build N' Build Forum